Email authentication is a process used by companies to verify the identity of the sender of an email.
It is becoming increasingly important due to the rise of phishing attacks, where malicious actors attempt to gain access to sensitive data by impersonating a legitimate source.
Bellow is a image of authenticated email:
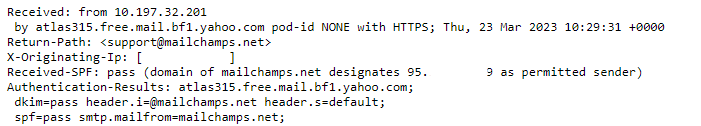
Email authentication is a security measure that verifies the identity of the sender. It works by having the sender prove they are who they say they are, typically by providing additional information such as a password, code, or digital signature. This additional information verifies that the sender is authorized to send the email, and that it is not a phishing attempt or other malicious activity.
The most common form of email authentication is SPF (Sender Policy Framework). This is a technology that helps prevent spoofing, where a malicious actor sends emails from an address that appears to be from a legitimate source. SPF works by checking the IP address of the sender, and verifying that it matches the legitimate source.
Another form of email authentication is DKIM (Domain Keys Identified Mail). This is similar to SPF, but instead of checking the IP address, it looks at the domain name of the sender. It then verifies that the message was sent from an authorized server and that it matches the domain.
How to implement spf and dkim?
1. Implement SPF:
SPF (Sender Policy Framework) is an email authentication standard used to protect against spoofing and phishing. To implement SPF, you will need to create a DNS TXT record that lists the IP addresses or subnets that are allowed to send emails from your domain. To create your SPF record, you will need to determine the IP addresses or subnets that are allowed to send emails from your domain. You can use the SPF Record Wizard provided by Microsoft to help you create the record. Once you have created the SPF record, you will need to add it to your domain‘s DNS records. Depending on your hosting provider, you may be able to do this yourself or you may need to contact your provider for help.
For steps follow this article
2. Implement DKIM:
DKIM (DomainKeys Identified Mail) is another email authentication standard used to protect against spoofing and phishing. To implement DKIM, you will need to create a DNS TXT record that contains a cryptographic signature used to verify that an email was sent from the domain it claims to be from. To create the DKIM record, you will need to generate a public/private key pair and use the